[春秋云实企安殿]SQLi
目录
[春秋云实企安殿]SQLi
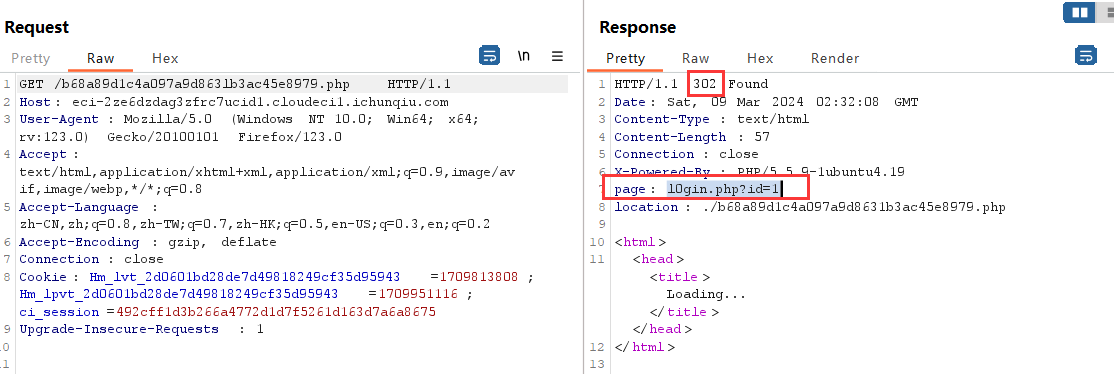
直接打开靶机地址会跳转到 /b68a89d1c4a097a9d8631b3ac45e8979.php ,查看页面源代码看到提示
而这正是个坑,真正有注入漏洞的地址在 302 回包的内容里
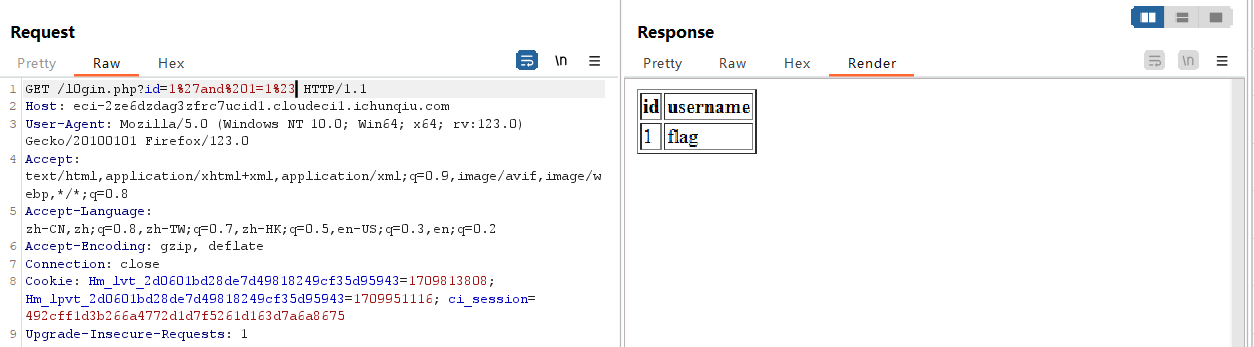
通过 /l0gin.php?id=1%27and%201=1%23 和 /l0gin.php?id=1%27and%201=2%23 可以判断存在 sql 注入漏洞且为字符型
/l0gin.php?id=1%27order%20by%202%23和/l0gin.php?id=1%27order%20by%203%23判断有2个回显位置
fuzz出逗号被截断,用无逗号注入
查库名
|
|
查表名
|
|
查flag
|
|
欲将心事付瑶琴。知音少,弦断有谁听?